Git Credentials
Overview of the Credentials tab, which permits access to Git Repositories in Typhoon Test Hub.
Git Credentials are used to access Repositories. In order to have access to clone a repository that is configured in a job, you must first add your credentials to Typhoon Test Hub.
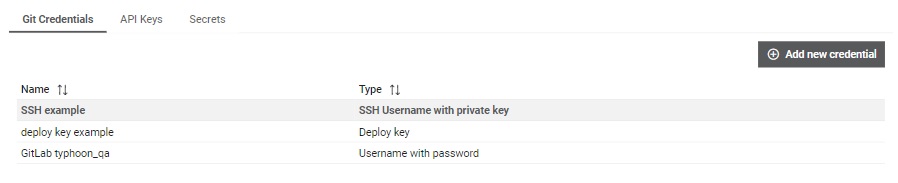
The Credentials table (Figure 1) shows the following information:
- Name
- Type
 button, columns of the table
can be customized - hidden or shown depending on the preference. Columns of the table
can be reordered by using drag and drop in the table header. When positioning cursor in
between two columns, cursor for column resizing will show and enable change of the
column's width. All changes made to the table will be automatically preserved.
button, columns of the table
can be customized - hidden or shown depending on the preference. Columns of the table
can be reordered by using drag and drop in the table header. When positioning cursor in
between two columns, cursor for column resizing will show and enable change of the
column's width. All changes made to the table will be automatically preserved.  button,
the Search input field is cleared and filtering is cancelled.
button,
the Search input field is cleared and filtering is cancelled. In the Details section, you can delete a credential by clicking on the  button.
A credential can only be deleted if there are no repositories connected with that
credential.
button.
A credential can only be deleted if there are no repositories connected with that
credential.
By clicking on a specific credential, you can open a form that will let you edit the credential details (Figure 2).
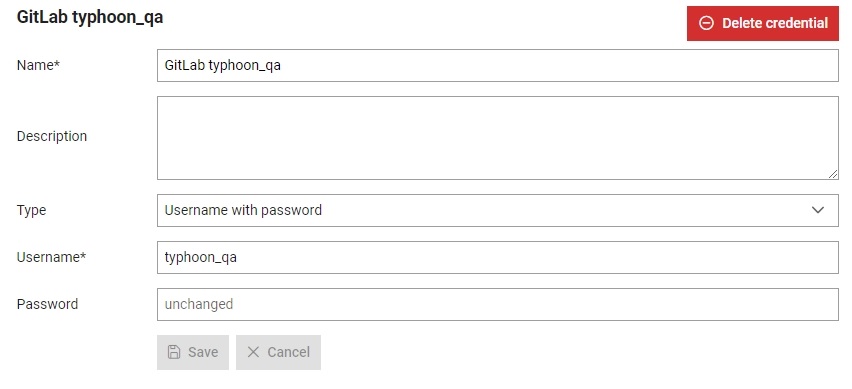
Create credentials
A new credential can be added by
clicking on the  button. This will open a form that lets you add information to set up your new credential (Figure 3).
button. This will open a form that lets you add information to set up your new credential (Figure 3).
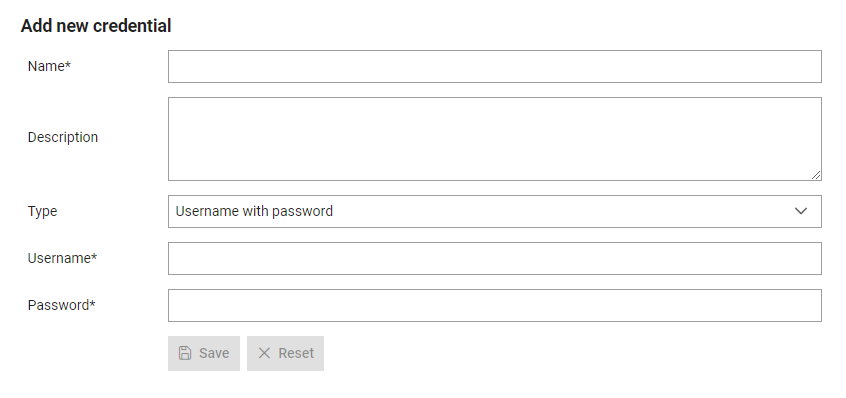
To set up a credential, you must:
- Give it a name which will be used to refer to it throughout Typhoon Test Hub. Each name must be unique.
- Write a description of the credential.
- Select the type of credential:
- Username and Password: Enter your username and password from
your account. Note that different platforms have specific requirements:
- GitHub: Username and password are no longer supported. You must use a personal access token (PAT) for authentication. Generate a PAT and use it instead of your password. For more information, visit the GitHub Authentication Documentation.
- GitLab: You can use a personal access token (PAT) instead of your password for secure authentication. Ensure you create a PAT with the required scopes. For more details, see the GitLab Cloning Documentation.
- Bitbucket: Use an app password for authentication. Create an app password in your Bitbucket account settings and use it instead of your regular password. For instructions, refer to the Bitbucket Documentation.
- Azure DevOps: You can use either a personal access token (PAT) or SSH keys for authentication. For a PAT, generate one in your Azure DevOps account and use it in place of your password. For SSH, make sure your key is added to your Azure DevOps account. More details are available in the Azure DevOps Authentication Overview.
- AWS CodeCommit: Use HTTPS with your IAM user credentials or SSH for secure access. For HTTPS, use your IAM user credentials or generated access key and secret key. For SSH, ensure your key is associated with your IAM user. Detailed instructions can be found in the AWS CodeCommit Documentation.
- SSH with private key or Deploy key: Paste the private part of your SSH key, and enter your passphrase if there is one. Be sure that there are no spaces at the end when adding a private key; to avoid this issue, it is recommended that you copy your key with the select all option and paste it directly into this input field. Also, it is important that the public part of your SSH key is added to your Git repository (if using deploy key) or account (if using SSH key).
- GitHub App: Insert App ID and paste the private key that is obtained from GitHub.
- Username and Password: Enter your username and password from
your account. Note that different platforms have specific requirements:
Note on storing credentials
When Typhoon Test Hub is installed, it generates an application key and stores it in a file on the server. Each credential is encrypted before storing it to the database. This encryption uses the application key that is stored on the server with Test Hub. When a user views or edits credentials, they are fetched from the database and only the username is decrypted and sent to the frontend.
When Computers are created, a secret key is generated for each one. This secret key is used to encrypt sensitive information that is sent between Test Hub and Officer. This is why Officer is started with a secret key parameter. For example, when a job is suppose to clone a repository, Test Hub will fetch credentials from the database, decrypt them using an application key, then encrypt them using the Officer (computer) secret key and send them with the repository information to Officer. When Officer receives the repository and credentials, it decrypts them to execute the clone command and then discards the encrypted data. Once the clone command is executed, the content of the cloned repository is then used by the Agent.
Using Deploy keys in GitHub
A deploy key is an SSH public key that grants read-only or read-write access to a single GitHub repository. Deploy keys are commonly used by automation tools, continuous deployment systems, or read-only access scripts that need to access a repository without using a personal user account or access token.
Deploy keys are repository-specific and are not tied to a GitHub user. This makes them ideal for securely granting external systems access to a repository without exposing user credentials.
To set up a deploy key in GitHub:
- Generate an SSH key pair on the system that needs access to the repository,
using a command like
ssh-keygen -t rsa -b 4096 -C "deploy-key". Do not add a passphrase (it is optional), and save the private key securely. - Copy the contents of the public key file (usually
id_rsa.pub). - Navigate to the repository on GitHub where the deploy key should be added.
- Go to Settings > Deploy keys.
- Click Add deploy key.
- Provide a title for the key, paste the public key into the key field, and select whether the key should have read-only or read/write access by checking the Allow write access box if needed.
- Click Add key to save it.
After setup, the system can use the associated private key to clone or pull from the repository over SSH. Deploy keys cannot be reused across multiple repositories; each repository requires a separate key. Now you can create new Git credentials with Deploy key type on Typhoon Test Hub with recently geenrated private key.
GitHub App authentication
GitHub Apps offer a secure and flexible way to integrate with GitHub's API and automate workflows. Unlike personal access tokens (PATs), GitHub Apps are scoped to specific repositories or organizations, use short-lived tokens for increased security, and offer fine-grained permissions.
Before authenticating as a GitHub App, you must first create and configure the App from your GitHub account or organization settings. Follow these steps to create a GitHub App:
- Navigate to Settings (of your GitHub account or ORganization), then GitHub Developer Settings and GitHub Apps.
- Select New GitHub App option
- Fill out the form with the required information:
- App name: A descriptive name for your integration.
- Homepage URL: A valid URL (your application homepage or company site).
- Permissions: Grant necessary permissions such as:
- Repository permissions → Contents → Read-only
- Any other permissions required by your use case
- Click Create GitHub App to finalize creation.
- Once the app is created:
- Record the App ID (you will use this later).
- Generate a private key (.pem file; you will use this later). Download and store it securely.
With your GitHub App created and the private key downloaded, you are now ready to install the app on a repository or organization. After creating your GitHub App, you must install it on the repositories or organizations where you want it to operate. This installation step grants the app access based on the permissions defined during creation.
- From the GitHub App management page, click on Install App in the left sidebar.
- Choose where to install the app:
- You can install the app on your personal account, an organization you manage, or specific repositories.
- You may choose to give access to All repositories or Only select repositories.
- Confirm the installation.
After installation, your GitHub App is now associated with the chosen repositories or organizations. Now you can create new Git credentials with GitHub App type on Typhoon Test Hub with recently obtained App ID and private key.